No matter whether you?�re seeking to diversify your copyright portfolio or allocate a part of your belongings right into a stablecoin, like BUSD, copyright.US lets clients to convert in between in excess of 4,750 convert pairs.
When they'd access to Secure Wallet ?�s program, they manipulated the consumer interface (UI) that shoppers like copyright staff would see. They changed a benign JavaScript code with code designed to change the meant place from the ETH inside the wallet to wallets managed by North Korean operatives. This malicious code would only goal distinct copyright wallets in contrast to wallets belonging to the different other buyers of this System, highlighting the specific character of this assault.
2. copyright.US will deliver you a verification e-mail. Open the e-mail you made use of to join copyright.US and enter the authentication code when prompted.
copyright partners with main KYC distributors to deliver a speedy registration course of action, so you're able to validate your copyright account and buy Bitcoin in minutes.
Some cryptocurrencies share a blockchain, while other cryptocurrencies work on their own different blockchains.
Security commences with understanding how developers acquire and share your facts. Details privateness and security methods could range dependant on your use, region, and age. The developer furnished this info and could update it with time.
Given that the danger actors engage Within this laundering method, copyright, legislation enforcement, and companions from throughout the sector continue on to actively do the job to Get better the resources. Having said that, the timeframe where funds can be frozen or recovered moves rapidly. Within the laundering process you will find three main levels where by the cash might be frozen: when it?�s exchanged for BTC; when It truly is exchanged for the stablecoin, or any copyright with its worth attached to secure belongings like fiat currency; or when It is cashed out at exchanges.,??cybersecurity actions may well turn out to be an afterthought, particularly when providers lack the funds or personnel for these kinds of steps. The problem isn?�t special to All those new to business; nevertheless, even properly-recognized companies might Allow cybersecurity drop on the wayside or may well absence the instruction to understand the quickly evolving threat landscape.
Given that the window for seizure at these levels check here is incredibly small, it involves economical collective action from law enforcement, copyright products and services and exchanges, and Intercontinental actors. The more time that passes, the more challenging Restoration gets.
On February 21, 2025, when copyright workers went to approve and sign a regimen transfer, the UI confirmed what appeared to be a authentic transaction Along with the intended destination. Only following the transfer of funds into the hidden addresses established through the destructive code did copyright staff realize a thing was amiss.
If you don't see this button on the home website page, simply click the profile icon in the top proper corner of the house web site, then choose Identification Verification from the profile page.
Several argue that regulation productive for securing banking companies is significantly less productive in the copyright Area a result of the field?�s decentralized mother nature. copyright requirements a lot more protection restrictions, but it also requirements new answers that bear in mind its dissimilarities from fiat financial establishments.
 Haley Joel Osment Then & Now!
Haley Joel Osment Then & Now! Joseph Mazzello Then & Now!
Joseph Mazzello Then & Now!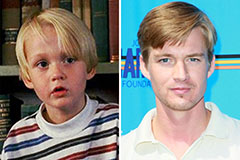 Mason Gamble Then & Now!
Mason Gamble Then & Now! Val Kilmer Then & Now!
Val Kilmer Then & Now! Jeri Ryan Then & Now!
Jeri Ryan Then & Now!